Trusted Platform Module (TPM)
TPM is a chip on the motherboard that provides security functions.
It's important to keep in mind that TPM is just a tamper proof recorder. TPM doesn't do any verification of the data being written to it. It's important to understand that TPM doesn't do anything by itself. The clients of TPM must use the functionalities by invoking the methods exposed by TPM.
The word "platform" in TPM refers to the entire hardware and software that's running on the computer on which the TPM is hosted.
It provides a way to secure everything that's running on that platform.
Endorsement Key
This is a certificate generated by the TPM manufacturer to identify a physical device.
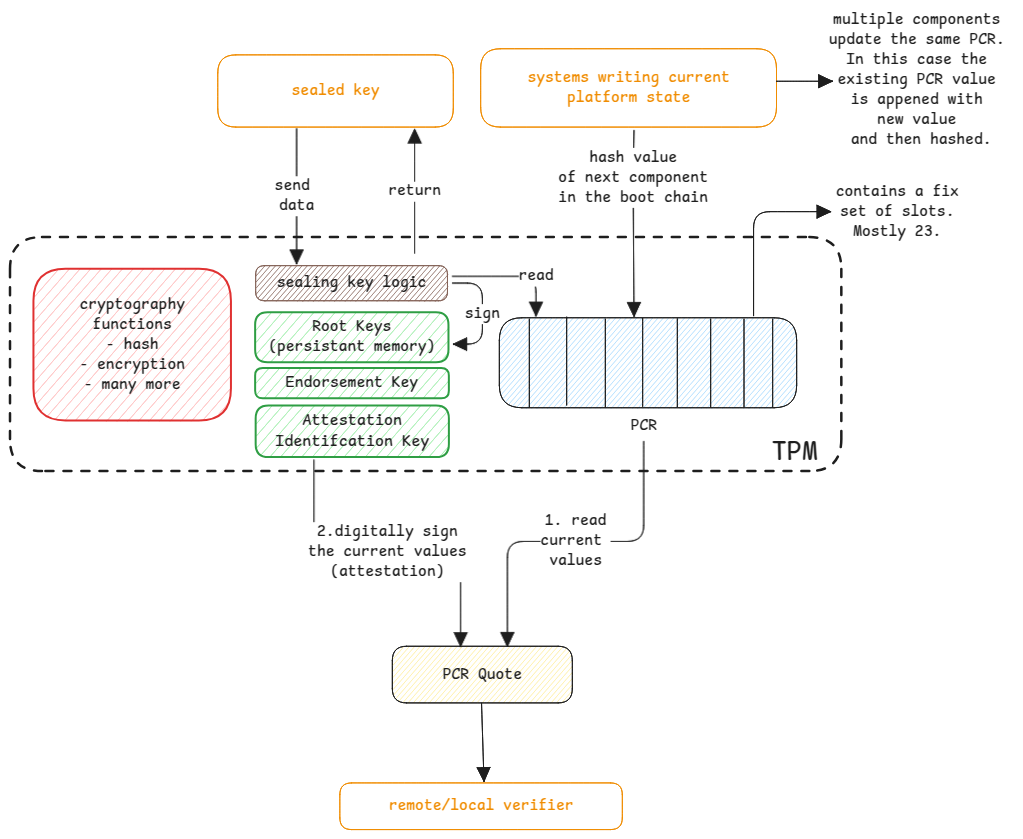
Platform Configuration Register (PCR)
This is the volatile memory of the TPM. The data here is written by each component of the platform during boot. Each component in the boot chain, measures the next component that it's going to execute and writes the hash of that measurement to a specific PCR slot.
Each component measures the next component that it's going to execute.
It basically represents the state of the platform at a given time.
The PCR is written to by the platform components, such as the BIOS, bootloader, and operating system, BitLocker PIN, etc.
The standards are defined already on who writes to which block of PCR. So every underlying part of the platform is aware of what and where it should write to PCR.
Every part of the platform that writes to PCR, always calculates the state of the next component that it will execute and creates an hash of that component and write to its PCR slot. This means, any small change will change the hash and thus the PCR value.
Extending Values
A specific PCR value of a slot is updated by multiple stages of the boot process.
Example, the operating system will extend the PCR value with the hash of the kernel,
and then the kernel will extend it with the hash of the initrd, systemd and many more.
This is done using the TPM2_Extend command, which appends the new hash to the existing PCR value.
This way, the PCR value is a cumulative hash of all the components that have been measured during the boot process.
Initial value of PCR is always 0x00. This is set during the reboot of the system.
Use cases of TPM
- Sealed key - for locally running applications.
- Attestation - for remote verification of PCR values.
Key Attestation
Each client of the TPM must ask for it's own AIP Public and private key pair. The client gets the public key (similar to SSL CSR) and send this to privacy CA to get a certificate for it. This is called Key Attestation where the key provided by the TPM is attested by the CA and provides
All quote responses are then signed with this private key from TPM and the response's digital signature is verified using the public key.
Attestation here is same as the real world attestation, where a trusted entity verifies the authenticity of a claim.
In this case, the certificate is issued by TPM, attested by privacy CA and verifier relies on attestation.
Real world example - College issues certificate, Government Authority attests it, third party relies on the attestation.
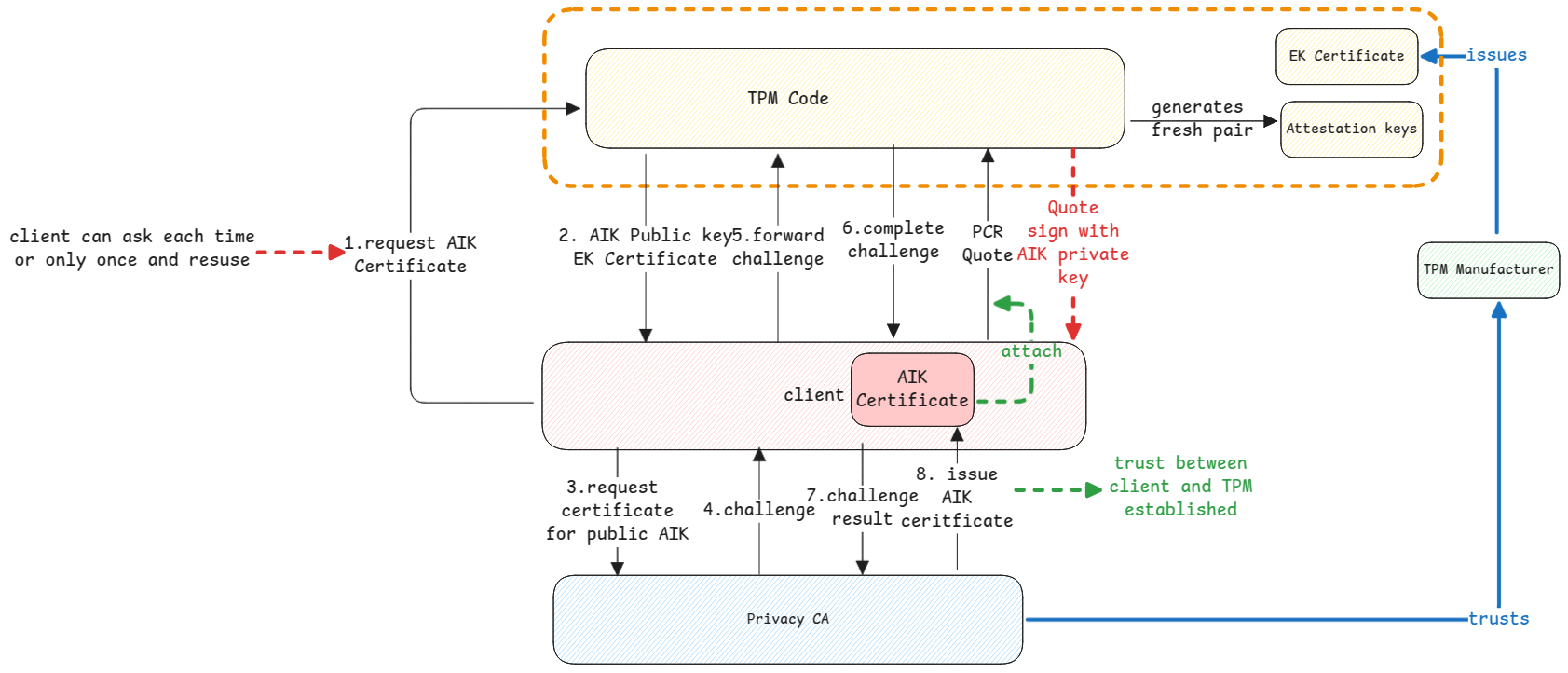
PCR Quotes and Signing
PCR quotes is nothing but the current values of PCR values. But the quote isn't returned as is. It's digitally signed using the private AIK of the client requesting it. The verifier then gets the corresponding certificate from client (which was already attested) and verifies the signature to trust the PCR quote values.
Attestation key is used only for digitally signing. It's never used for encryption.
Attestation Report
Attestation Report is just an extended report of the PCR quotes. It has more information on the history, timestamp, etc. Rest of the signing, certificate process remains same.
Sealed Key
This is a feature that's used to protect sensitive data using TPM. This is the feature used by BitLocker to encrypt the disk encryption key. The sealed key feature can be used by any application to store a secret.
Generation - Send key to be sealed -> Encrypt Key -> Attach PCR values -> Return Sealed Key.
Reading - Send Sealed Key -> Decrypt Key -> Verify PCR values -> Return original key if PCR values match.
Here, the system asking for a sealed key must inform which PCR values must be used to seal the key. This is nothing but the PCR policy.
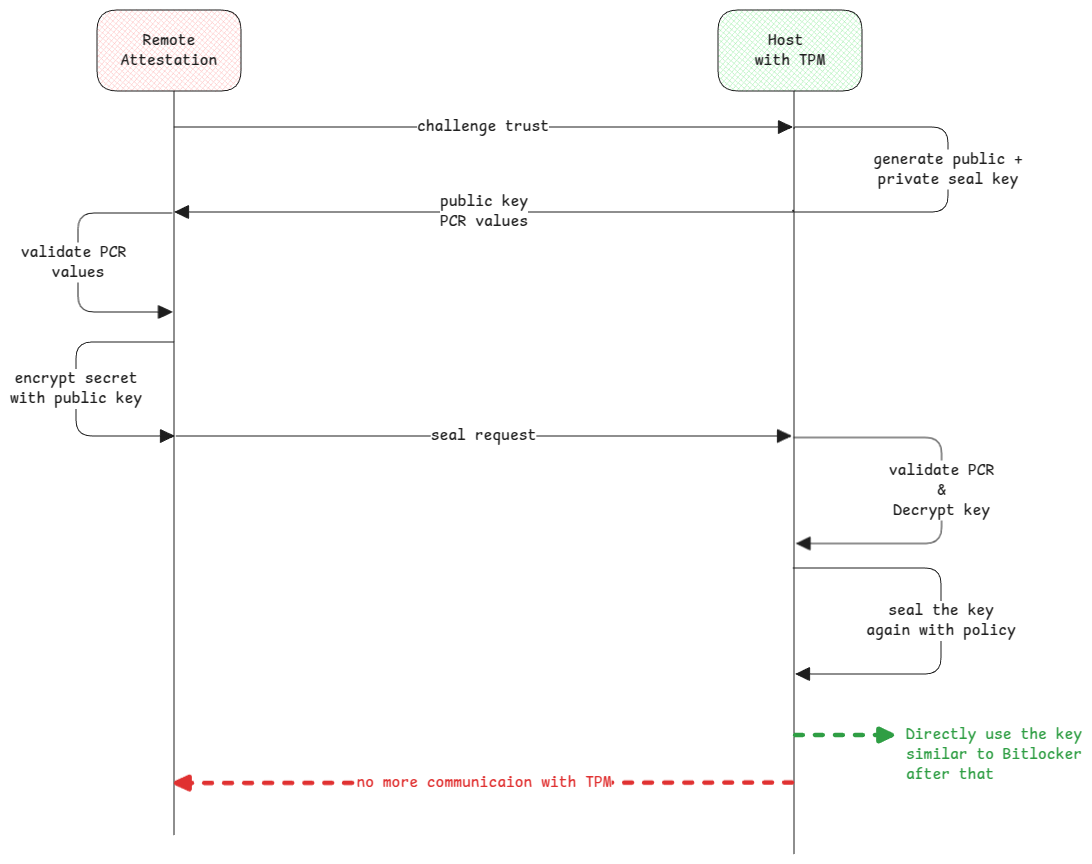
Remote Sealing
This means, the remote system must first trust the TPM and then create a local seal on the TPM.
In case of local sealing process used by BitLocker, the key is generated locally and sealed in the TPM.
But in case of remote sealing, a remote system first has to trust the TPM and then asks the TPM to seal the key.
Roots of Trust
Static Root of Trust - Here the root of trust is the BIOS/UEFI and it assumes that the BIOS/UEFI are trustworthy.
The BIOS then measures bootloader and then bootloader measures OS Kernel and
the OS Kernel measures the next component in the boot process.
Dynamic Root of Trust - The root isn't trusted by default. The measurement happens from root.